DNS Records that are required for proper functionality of Active Directory
We know that DNS servers serves more than resolving Name to IP and IP into Name. It is core protocol or you can say daddy of all protocols over a network.
In this article I have tried to visualize and explain all the core records of DNS without which Active Directory cannot function properly.
Here are the list of all core SRV, A and C-Name records that are used by Active Directory and Domain clients.
Please Note: The Red marked records in below table are used by Non-SRV-Aware Clients
| Mnemonic | Type | DNS Record | Requirements |
|
SRV | _ldap._tcp.pdc._msdcs.<DnsDomainName> | One per domain |
|
SRV | _ldap._tcp.gc._msdcs.<DnsForestName> | At least one per forest |
|
SRV | _kerberos._tcp.dc._msdcs.<DnsDomainName> | At least one per domain |
|
SRV | _ldap._tcp.dc._msdcs.<DnsDomainName> | At least one per domain |
| A | <DomainControllerFQDN> | One per domain controller (domain controllers that have multiple IP addresses can have more than one A resource record) | |
|
A | gc._msdcs.<DnsForestName> | At least one per forest |
|
CNAME | <DsaGUID>._msdcs.<DnsForestName> | One per domain controller |
Below I have mentioned the location of all these important records, with their properties and NSLOOKUP commands to verify if the record exists correctly or not. I have taken screenshot from a single domain lab, on default site i.e. my domain itself represent the forest. So results may vary if you explore these in big infrastructure.
In the records Properties window, you will notice below few fields:
Priority- The priority of the server. Clients attempt to contact the server with the lowest priority.
Weight – A load-balancing mechanism that is used when selecting a target host from those that have the same priority. Clients randomly choose SRV records that specify target hosts to be contacted, with probability proportional to the weight
Port Number- The port where the server is listening for this service.
Target – The fully qualified domain name of the host computer.
Host Records for SRV-Aware Clients
- PDC Record – _ldap._tcp.pdc._msdcs.<DnsDomainName>
Allows a client to locate the server that is acting as the primary domain controller (also known as a “PDC”) in the mixed-mode domain named in DnsDomainName . Only the PDC emulator master of the domain registers this SRV record.

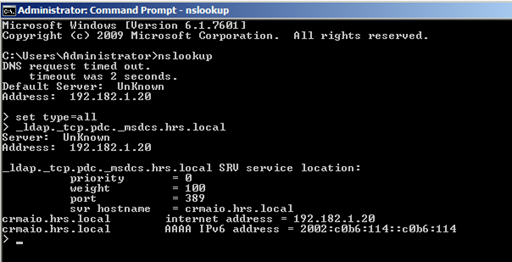
- GC Record – _ldap._tcp.gc._msdcs.<DnsForestName>
Allows a client to locate a Global Catalog (gc) server for this forest. Only domain controllers that are functioning as Global Catalog servers for the forest named in DnsForestName register this SRV record.


- KDC Record – _kerberos._tcp.dc._msdcs.<DnsDomainName>
Allows a client to locate a domain controller that is running the Windows implementation of the Kerberos KDC service for the domain named in DnsDomainName . All Windows Server–based domain controllers that are running the KDC service (that is, that implement a public key extension to the Kerberos v5 protocol Authentication Service Exchange subprotocol) register this SRV record.


- DC Record – _ldap._tcp.dc._msdcs.<DnsDomainName>
Allows a client to locate a domain controller (dc) of the domain named by DnsDomainName . All Windows Server–based domain controllers register this SRV record.
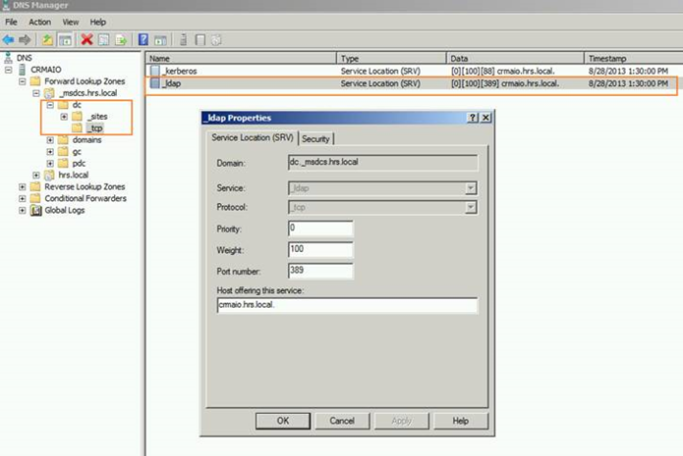
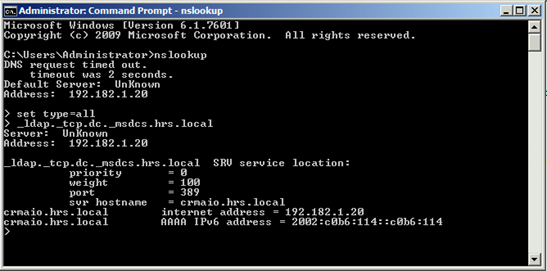
- Domain FQDN A Record – <DomainControllerFQDN>
This record helps to locate the domain controllers IP address in a domain.

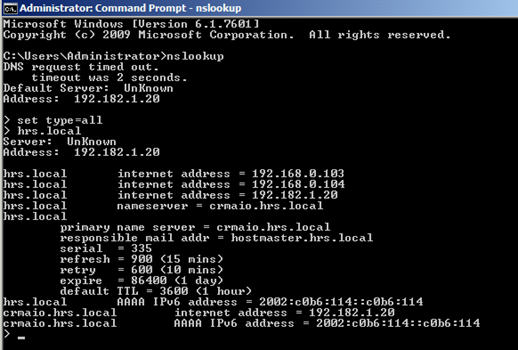
Host Records for Non-SRV-Aware Clients
- GC IP Address – gc._msdcs.<DnsForestName>
Allows a non-SRV-aware client to locate any Global Catalog server in the forest by looking up an A record. A name in this form is returned to the LDAP client through an LDAP referral. A non-SRV-aware client looks up this name; an SRV-aware client looks up the appropriate SRV resource record.
Net Logon also registers a DNS CNAME (alias) record for use by Active Directory replication The Locator does not use this record.


- DsaCname Record – <DsaGUID>._msdcs.<DnsForestName>
Allows a client to locate any domain controller in the forest by looking up an A record. The only information that is known about the domain controller is the GUID of the directory system agent (also known as the “DSA”) object for the domain controller and the name of the forest in which the domain controller is located. This record is used to facilitate renaming a domain controller.


To know more about SRV records in DNS , please refer to below article
http://technet.microsoft.com/en-us/library/cc961719.aspx
For more article updates, videos and posters join our official page in Facebook
Facebook Page: https://www.facebook.com/ServerGeeks
Web Site: https://servergeeks.wordpress.com/
Video Channel: https://www.youtube.com/user/Habibmvp









